The Human Firewall: What is it, and how do you implement it?
Estimated reading time: 6 minutes
If you are an IT technician, you might find that an IT-related problem often exists between chair and keyboard. In other words: the problem is not caused by the computer system, but by its user. It often leads to you having to advise your colleagues to turn their device off and on again for the umpteenth time. But in some cases, a human error might jeopardize the entire organization’s cybersecurity. With the average costs of a data breach exceeding $3.9 million, it becomes evident why it is crucial to invest in a so-called Human Firewall.
What is the Human Firewall
But first, what does the Human Firewall mean? We define the Human Firewall as basically every human aspect in your cybersecurity. The ‘wetware’ in your network in addition to your hardware and software. Indeed, the Human Firewall is best described as the part between the chair and keyboard. That means you already have a Human Firewall, whether you were aware of it or not. If you were not aware before, chances are it is the weakest spot in your cybersecurity.

It is hard to say how many cybersecurity incidents are caused by human error exactly. Still, various researches found astonishing numbers, ranging from over 50 percent of incidents as a result of inappropriate IT resource use by employees (Kaspersky) to even 90 percent of cyber data breaches caused by human error (CybSafe). It seems the old wisdom ‘Failing to plan is planning to fail’ really applies here.
Much like a lock on a door, a traditional firewall typically guards your trusted inner network against untrusted outer intrusion. Yet even the best lock is useless when someone forgets to close the door. In terms of cybersecurity, that translates to an accidental click on a phishing link, an unsafe password, or a postponed security update, enabling malicious people to bypass your carefully implemented cybersecurity measures. If you never planned for such a scenario and only paid attention to your traditional firewall, you are planning to fail. However, by strengthening your Human Firewall, you make sure no metaphorical doors or windows are left unchecked, creating an extra layer of security.
Train the Human Firewall
The Human Firewall can only be strengthened through training. But do not go ahead to pick a yearly moment and try to cram all the required knowledge in just one hour just yet. It is way more efficient to spread out all the information and apply continuous learning. Here are a few reasons why:
- As soon as we stop learning, we start forgetting. This process is called the Forgetting Curve. You can break the downward trend by repeating information over and over. By repeating information, there is a better chance the recipient will understand and internalize it.
- Cybersecurity is constantly evolving. It is a cat-and-mouse game in which hackers try to find new exploits, while tech companies and IT professionals try to stay one step ahead of the malicious. Therefore, knowledge should be updated and refreshed continuously.
- There are numerous reasons why an employee might miss out on a scheduled training. Absenteeism, a day off, conflicting meetings, or even a new hire starting just a few days after the scheduled training; as soon as someone misses out on the training, they form a weak link.
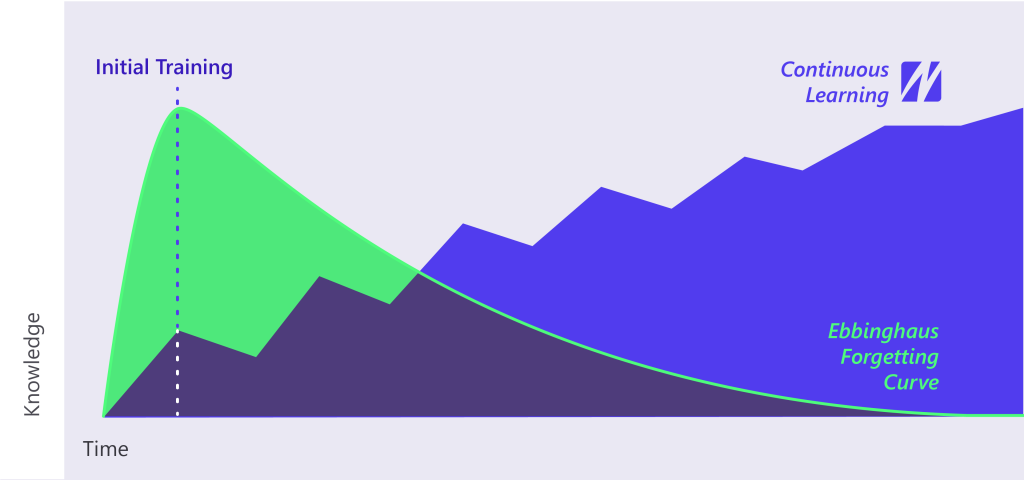
By breaking down cybersecurity awareness training in bite-sized pieces of information and gently repeating this information over an extended period using a multitude of output channels, you will safeguard a minimum level of knowledge and awareness and keep everyone informed about the latest threats.
When you use pulse surveys to measure your training results, you can even adjust your training intensity when needed. Just ask your employees a few cybersecurity questions every once in a while, and check if they know the ropes. If they do, great! If they don’t, you might want to crank your training up a little.
Don’t forget to include each and every employee. That means every single department, but also new hires. Your Human Firewall training should become an integral part of your employee onboarding. Your employees are all part of the Human Firewall, so they should all receive the same training. After all, a chain is only as strong as its weakest link.
Example of a Human Firewall
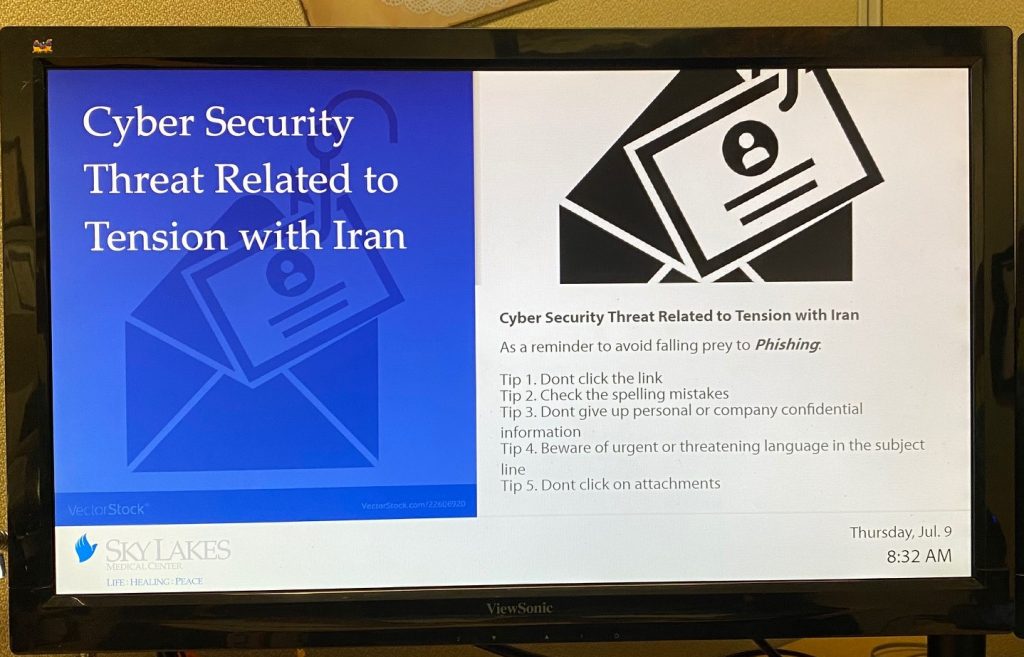
To give an example of the Human Firewall and how continuous training contributed to its strength, we asked one of our clients how they did it. For American-based Sky Lakes Medical Center, the protection of patients’ Electronic Medical Records is vital. To strengthen their defense against potential cyber-attacks, they use Netpresenter to increase cybersecurity knowledge among all employees.
Sky Lakes Medical Center now continuously shows messages about spam, sharing passwords, and other security concerns. This way, they raise the staff’s awareness of cybersecurity risks, helping Sky Lakes as a whole keeping the Electronic Medical Records of their patients safe. Sky Lakes even calls it ‘an easy and efficient way to educate our staff on all the security risks.’
Are you, just like Sky Lakes, looking for a way to build your Human Firewall? Get in touch with our consultants and find out how Netpresenter can help your organization accomplish this! Or download our free checklist on cybersecurity.